Safeguarding Your Company in the Digital Era: Managing Typical Network Vulnerabilities
Today’s ever changing virtual environment presents businesses with a wide range of cybersecurity risks. The possibility of data breaches and network invasions is quite real for organizations in all industries, ranging from insider threats to contemporary cyberattacks.
As the United Arab Emirates (UAE) keeps to encompass virtual transformation and technological innovation, safeguarding touchy statistics and maintaining the integrity of digital belongings have become paramount concerns for corporations of all sizes.
In this blog, we will discover 5 common network vulnerabilities that organizations regularly forget about and provide actionable insights and strategies for addressing them.
From the importance of multifactor authentication (MFA) to the dangers associated with obsolete technology and lazy patching practices, we’re going to delve into key cybersecurity annoying conditions going through companies inside the UAE. Additionally, we’re going to observe the growing threats in cloud safety and the crucial role of email protection in defending in competition to phishing attacks and social engineering methods.
As businesses navigate the complexities of the virtual landscape, partnering with managed offerings vendors like TLS-IT can offer beneficial steering in strengthening cybersecurity defenses and mitigating chances.
By adopting a proactive technique to cybersecurity and enforcing satisfactory practices for community security, agencies can decorate their resilience in opposition to cyber threats and guard their essential property efficiently.
Come along as we explore the field of cybersecurity and learn useful strategies for protecting your company in the digital era. We’ll provide you with the knowledge and tools you need to stay ahead of cyber adversaries and ensure the security of your company’s digital infrastructure, from enforcing strict authentication policies to conducting routine protection assessments and employee training programs.
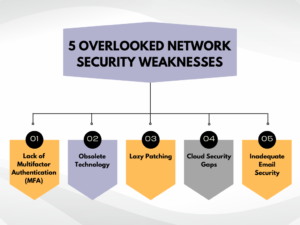
1. Lack of Multifactor Authentication (MFA):
Multi Factor authentication (MFA) is a critical defense mechanism against unauthorized access to your business systems. In the UAE, where digital transformation is rapidly reshaping industries, MFA is indispensable for protecting sensitive data and intellectual property.
It adds an extra layer of security beyond passwords, making it significantly harder for cybercriminals to breach your network. Businesses can implement MFA across various platforms and applications, including email, cloud services, and remote access tools. By leveraging biometric authentication, one-time passcodes, or hardware tokens, organizations can strengthen their authentication processes and reduce the risk of account compromise.
2. Obsolete Technology:
Businesses in the UAE face serious security threats due to outdated software and hardware. Rapid technological advancement makes outdated systems more susceptible to cyberattacks.
Keeping up with technological infrastructure is crucial in industries like banking, healthcare, and government where data protection and regulatory compliance are crucial. Companies should routinely evaluate their IT resources, identify out-of-date parts, and rank the importance of upgrading or replacing them.
Additionally, modernization efforts like cloud migration and digital transformation can improve security posture and help future-proof your company’s IT infrastructure.
3. Lazy Patching:
A crucial cybersecurity procedure that many businesses ignore or undervalue is patch management. Timely patching is essential to limiting vulnerabilities and decreasing the attack surface in the highly dynamic corporate landscape of the United Arab Emirates, where cyber threats are continually changing.
Companies should set up effective patch management procedures, such as automated distribution systems, periodic vulnerability assessments, and patch prioritization depending on severity. Furthermore, ensuring the integrity of crucial IT systems and reducing the chance of system interruptions can be achieved by thoroughly testing and validating patches prior to deployment.
4. Cloud Security Gaps:
The UAE is seeing a rapid increase in cloud use due to the demand for scalability, agility, and cost effectiveness. Moving to the cloud, however, comes with additional security threats and concerns.
To protect their data and apps, businesses need to take a proactive approach to cloud security by utilizing cutting-edge technologies and industry best practices. This entails putting strong identity and access management (IAM) rules in place, encrypting data while it’s in transit, and keeping an eye out for strange activity in cloud settings.
Additionally, companies should work with reputable cloud service providers, regularly audit their cloud security, and keep up with new threats and vulnerabilities in the cloud ecosystem.
5. Inadequate Email Security:
Email is still one of the attack channels that hackers use the most. Organizations of all sizes continue to face serious risks from phishing assaults, in particular.
Businesses should invest in complete email security solutions that include spam filtering, advanced threat detection, and user awareness training in order to reduce the risk of email-based risks.
Programs for employee education and awareness are essential in enabling employees to identify and report phishing attempts, malware attachments, and dubious URLs.
Furthermore, email spoofing and domain impersonation attacks can be avoided by putting email authentication methods like DMARC (Domain-based Message Authentication, Reporting, and Conformance) into practice.
In addition to addressing those common network vulnerabilities, companies in the UAE must prioritize cybersecurity hygiene and resilience-constructing measures, together with:
Employee Training and Awareness: Regular cybersecurity schooling and consciousness applications to educate personnel approximately the modern day threats, phishing strategies, and high-quality practices for maintaining protection.
Endpoint Security: Deploying endpoint safety answers such as antivirus software, intrusion detection structures, and endpoint encryption to secure gadgets and endpoints against malware and cyber threats.
Data Encryption: Implementing encryption technology to defend touchy information each at relaxation and in transit, making sure confidentiality and integrity across the company.
Incident Response Planning: Developing and regularly checking out incident reaction plans to efficiently stumble on, comprise, and mitigate security incidents and statistics breaches.
By adopting a holistic technique to cybersecurity and investing in proactive safety features, agencies within the UAE can toughen their resilience against cyber threats and shield their digital assets correctly. With the aid of relying on cybersecurity partners like TLS-IT, businesses can navigate the evolving threat landscape with self assurance and live ahead of cyber adversaries.
Conclusion-
By adopting a holistic approach to cybersecurity and investing in proactive security measures, companies in the UAE can strengthen their resilience against cyber threats and protect their digital assets effectively. With the assistance of cybersecurity partners like TLS-IT, businesses can navigate the evolving threat landscape with confidence and stay ahead of cyber adversaries. Reach out to us at (+971) 43955877 for expert consultation and configuration assistance. Our committed team is at your service round the clock, providing continuous guidance and support.




